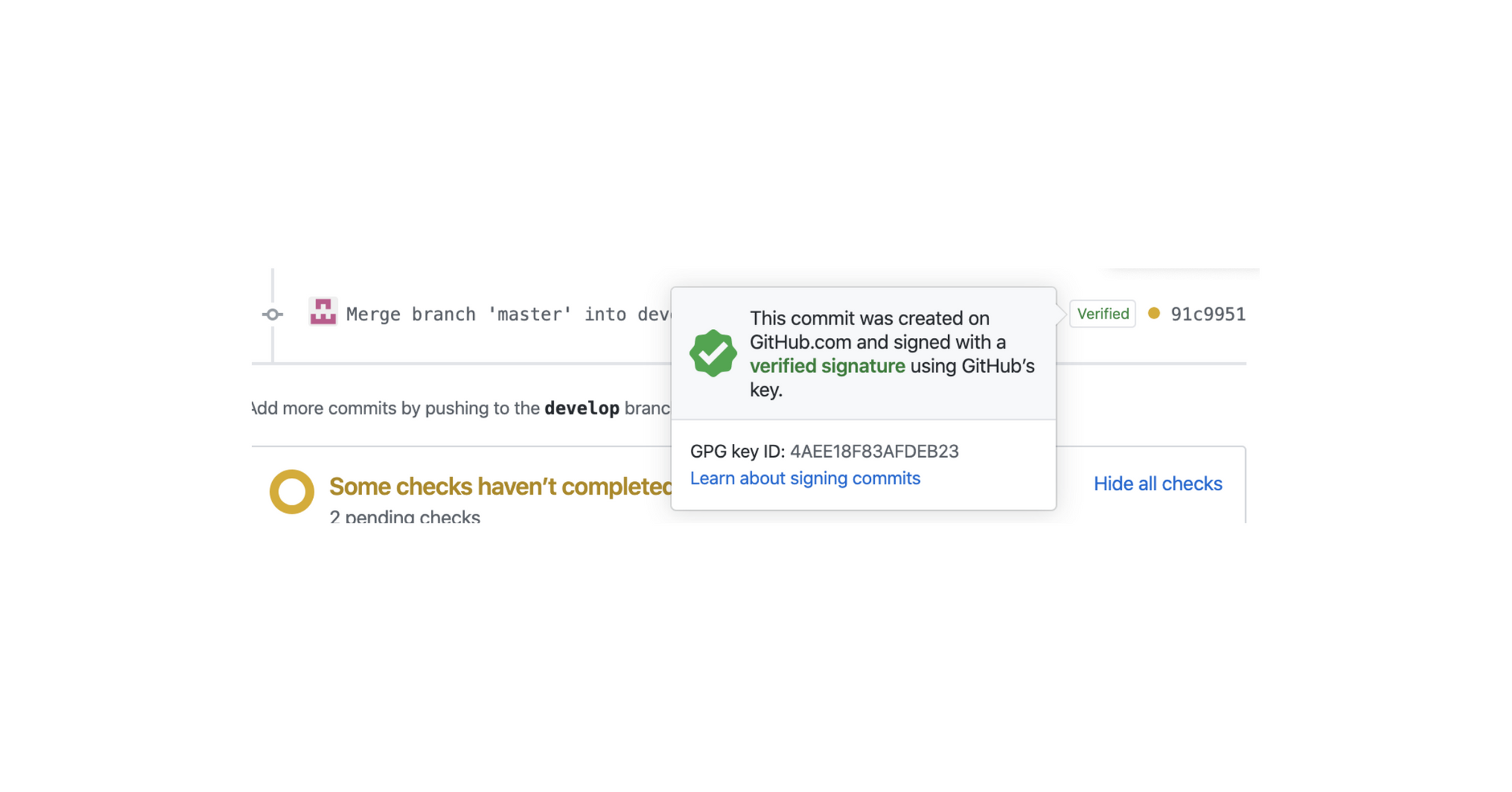
I recently resolved a conflict on Github and became curious after seeing the image above. It got me thinking. I want to sign my commits, too. This article summarizes the steps I took to sign my commits and tags on Git using GPG.
Using GPG or S/MIME, you can sign tags and commits locally. These tags or commits are marked as verified on GitHub so other people can trust that the changes come from a trusted source.
- Github
Installing GPG using HomeBrew
You should have HomeBrew installed, first. Open your terminal and enter the following.
brew install gpgGenerating GPG Key
To generate a GPG key, run gpg --full-generate-key. When prompted, use the default kind of key and use 4096 as key size.
% gpg --full-generate-key
gpg (GnuPG) 2.2.19; Copyright (C) 2019 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(14) Existing key from card
Your selection?
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Ronie Martinez
Email address: ronmarti18@gmail.com
Comment:
You selected this USER-ID:
"Ronie Martinez <ronmarti18@gmail.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.You will be prompted for a passphrase that you will use with the GPG key.

After entering your passphrase, your key will be generated.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: key FBD003C43EEB1AE9 marked as ultimately trusted
gpg: revocation certificate stored as '/Users/roniemartinez/.gnupg/openpgp-revocs.d/31543A183947814A11FE********************.rev'
public and secret key created and signed.
pub rsa4096 2020-03-15 [SC]
31543A183947814A11FE********************
uid Ronie Martinez <ronmarti18@gmail.com>
sub rsa4096 2020-03-15 [E]Listing GPG key
To list your keys, run gpg --list-secret-keys --keyid-format LONG.
% gpg --list-secret-keys --keyid-format LONG
/Users/roniemartinez/.gnupg/pubring.kbx
---------------------------------------
sec rsa4096/FBD003C43EEB1AE9 2020-03-15 [SC]
31543A183947814A11FE********************
uid [ultimate] Ronie Martinez <ronmarti18@gmail.com>
ssb rsa4096/B3BF1247******** 2020-03-15 [E]
Acquiring the public key in plaintext
You will be needing the plaintext GPG public key to be used with Github
% gpg --armor --export FBD003C43EEB1AE9
-----BEGIN PGP PUBLIC KEY BLOCK-----
<plaintext key should be here>
-----END PGP PUBLIC KEY BLOCK-----Go to https://github.com/settings/gpg/new and paste the generated block above.
Setting git signing key
To setup GPG signing with git, enter the commands below.
git config --global user.signingkey FBD003C43EEB1AE9
git config --global commit.gpgsign true
git config --global gpg.program gpgA fix for OSX users
There is an existing issue for Git GPG signing on Mac OSX wherein signing fails when you commit.
error: gpg failed to sign the data
fatal: failed to write commit objectTo fix this, do the following:
brew install pinentry-mac
echo "pinentry-program /usr/local/bin/pinentry-mac" >> ~/.gnupg/gpg-agent.conf
killall gpg-agentCommit your changes
When you commit your changes, you will be prompted for your passphrase. You may optionally tick Save in Keychain to prevent passphrase prompts.

Verifying signed commit
Run git log --show-signature -1 to see the signature of the last commit.
% git log --show-signature -1
commit 6300b56a5be9df447788bfadccf78b8fe34e2ab4 (HEAD -> develop, origin/develop)
gpg: Signature made Sun Mar 15 15:30:05 2020 PST
gpg: using RSA key 31543A183947814A11FE0EBFFBD003C43EEB1AE9
gpg: Good signature from "Ronie Martinez <ronmarti18@gmail.com>" [ultimate]
Author: Ronie Martinez <ronmarti18@gmail.com>
Date: Sun Mar 15 14:47:38 2020 +0800
Remove coverage from dev dependencies
- Update .travis.yml
- Update dependencies
Push your commit to Github. You will be able to see the "Verified" badge next to your commit.

Signing tags
When signing tags, add the -s flag. Run git tag --help to know more.
git tag -s -a 2.8.11 -m "Release 2.8.11"Verifying signed tags
To verify GPG signature of your tags, use the -v or --verify flag.
% git tag -v 2.8.11
object 34f07b3cb2e5125545ee524615f84b5ed059f767
type commit
tag 2.8.11
tagger Ronie Martinez <ronmarti18@gmail.com> 1584258725 +0800
Release 2.8.11
gpg: Signature made Sun Mar 15 15:52:05 2020 PST
gpg: using RSA key 31543A183947814A11FE0EBFFBD003C43EEB1AE9
gpg: Good signature from "Ronie Martinez <ronmarti18@gmail.com>" [ultimate]Another way is to check the tag section in your Github repository which should show a "Verified" badge on the right side corner.

References
- Git Tools - Signing Your Work
- Generating a new GPG key
- Stack Overflow - gpg failed to sign the data fatal: failed to write commit object